An enforcement-based approach to security begins with a security policy backed by security controls, often heavy-handed and designed to prevent employees from engaging in risky behavior.
Most organizations exclusively use enforcement-based security controls, usually carried out on the network level with a Cloud Access Security Broker (CASB) or a Security Services Edge (SSE). CASBs secure data between on-premises and cloud architectures, validate authorization rules, and access controls against the company’s security policy. Some organizations also use CASBs to block SaaS applications, but like SSEs, CASBs only support some applications.
Unmanageable applications and security
The applications these tools don’t support are often the riskiest because they don’t meet common industry and security standards, including SAML for authentication and SCIM for user management. At Cerby, we call these “unmanageable applications,” and according to our research, 61% of SaaS applications are unmanageable. Unmanageable applications are popular, and in a post-COVID-19 world, the rate at which employees buy and deploy them has reached a new height.
Pre-COVID-19, IT departments were primarily responsible for purchasing and deploying organization-wide applications. The shift to remote work empowered employees across organizations to select their tools. At the same time, rapid digitization gave them a wider selection of tools to choose from causing a surge in unmanageable applications.
The average user doesn’t typically think about security first–and why should they? Most people tend to assume applications are secure, and some might not care about security at all. Most users care about user-friendly features, design aesthetics, and convenience. To meet these changing requirements, application vendors altered their product roadmaps; for many of them, security was no longer a top priority.
Whether employees know it or not, unmanageable applications can negatively affect an organization’s overall security and often create more work for technology teams. Someone has to monitor for unmanageable applications, manually enable features like two-factor authentication (2FA), and enforce strong passwords.
To remove the burden, many organizations simply block or ban unmanageable applications.
It’s entirely understandable why organizations take this approach–it’s a quick fix to an immediate and concerning problem. However, as a long-term, comprehensive solution, a purely enforcement-based system isn’t sustainable or practical.
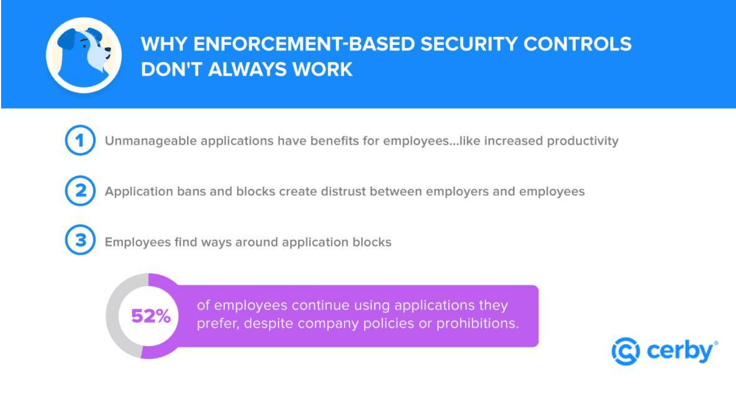 Employees like choosing their work applications, and 92% of employees and managers want full control over application choice. This behavioral change creates some unexpected challenges for organizations with an enforcement-based approach.
Employees like choosing their work applications, and 92% of employees and managers want full control over application choice. This behavioral change creates some unexpected challenges for organizations with an enforcement-based approach.
For instance, many employees using banned or blocked applications also attempt to manage access manually, even when they’re ill-equipped to do so. According to our research, employees and managers are making access management up as they go, creating risk and exposure for organizations at every point of interaction.
So, what’s the solution? We believe that employers need a more practical and forward-facing posture–one that strikes a balance between employee application choice and employer priorities such as security and compliance.
An enrollment-based approach to security
An enrollment-based approach to cybersecurity empowers employees to actively participate in enterprise-wide security and compliance efforts. Unlike enforcement-based systems, an enrollment-based approach enables employees to choose the applications they want to use for work.
At Cerby, balancing enforcement and enrollment is the best answer for organizations and their employees. Employees should be able to choose their applications, and employers shouldn’t worry about security.
When employees understand that application choice comes with responsibility, security becomes everyone’s concern. When self-enrolling and registering applications is easy, the same employees who resent policies on application choice will willingly get on board with strengthening security and ensuring compliance.
Want to learn how you can empower your employees to use their favorite applications while keeping them secure with Cerby? Book a demo here!