Enterprise Password Managers (EPMs) have been a standard solution for managing passwords for years, but the time has come to seriously question their need and usefulness. Organizations have adopted more cloud-based applications as IT budgets have shifted into business units. However, most of these applications don't support identity standards, which is why EPMs exist.
According to our internal research at Cerby, 61% of applications don't support standards like single sign-on (SSO) for authentication (authN), and 94% don't support the System for Cross-Domain Identity Management (SCIM) for authorization (authZ), as shown in Figure 1.
EPMs exist because only a tiny fraction of applications support standards like SSO (authN) and SCIM (authZ). I refer to the applications that fall into this category as Unmanageable Applications. Gartner calls them nonstandard applications. They are a huge source of manual work, user experience pain, and risk for every enterprise.
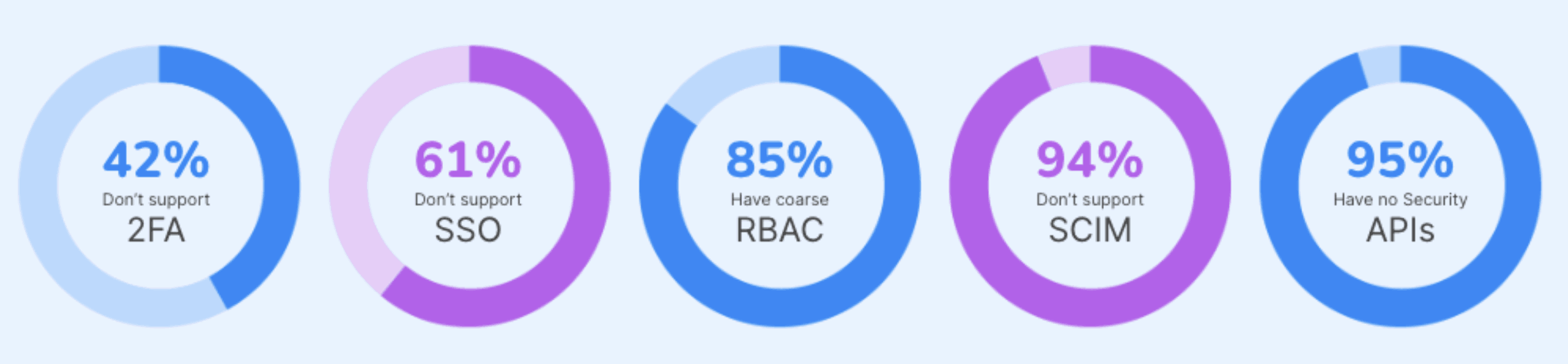 Figure 1. Security standards supported by the top 10,000 applications
Figure 1. Security standards supported by the top 10,000 applications
Source: Cerby Research
With so few applications supporting standards like SSO, it is no surprise that over half of all attacks are due to stolen credentials (Verizon DBIR, 2022). As the enterprise landscape has evolved along with threats, organizations need more comprehensive solutions that address provisioning, authentication, identity governance and administration, and privileged access management. The lack of integration of these capabilities in EPMs leaves organizations with a significant and widely exploited gap in their security and compliance posture.
The challenges with Enterprise Password Managers
The challenges with EPMs are many, but the heart of the problem is that they only address one tiny aspect of the identity and access management (IAM) lifecycle: the password. All other stages of the lifecycle are left to the end user, which means they must deal with a fragmented and terrible user experience. For instance, users may only need to remember the master password but are still left to manage critical security tasks like turning on two-factor authentication (2FA) for an account, updating passwords (ever tried manually rotating 400 passwords? Not a fun task), or removing access to an application for a former employee. EPMs also lack visibility into user access and activity. Many applications your teams use are a dark signal for your SIEM.
What you don't see can and will hurt you.
The future is not EPM, at least not as currently defined. The next generation of access management requires a more comprehensive approach. Chief Information Security Officers (CISOs) are increasingly looking for solutions that lower the total cost of ownership (TCO), increase productivity, and manage the unchecked risk of unmanageable applications.
What does the next generation of access management look like?
The next generation of access management must remove the dependency on the business user to carry out mission-critical security tasks. Next-gen solutions must have advanced application catalogs with deep knowledge of thousands of applications. Also, solutions must be able to extend SSO and SCIM to any application, even when they don’t natively support those standards.
With capabilities like these, employees can access all their applications using a single set of credentials, whether cloud-based or on-premises. The need to carry out manual security tasks also completely disappears. This improves the user experience and makes it easier for organizations to move one step closer to passwordless authentication.
After personally spending years in the tech industry, first at Google and then as co-founder at Ooyala, my co-founders and I saw this problem firsthand over and over. The founding team, including myself and Vidal González, decided it was time to fix this problem and build a company that flips the script: a solution for unmanageable applications that eliminates the UX and security problems of EPMs and delivers visibility, control, automation, and a beautifully designed interface that every business user can quickly master.
How Cerby solves the problem associated with Enterprise Password Managers
Cerby provides more granular control over access, enabling organizations to control third-party access and automate user offboarding and onboarding. This tedious task costs organizations thousands of hours per year, not to mention security risks when someone leaves a company and retains their access. Cerby also provides an activity log of all access, which can be fed into a SIEM and other security tools for compliance and auditing purposes. This level of visibility and control is impossible with the current generation of EPMs.
Cerby also enables identity teams to get the most out of their IAM investments, such as Okta, Azure AD, and Ping, providing a comprehensive access management solution. Organizations can have a single point of control for all their access management needs, reducing the complexity and cost of managing multiple solutions.
Current-generation EPMs can no longer keep up with modern enterprise security needs. The proliferation of cloud-based applications that don’t support identity standards like SSO and SCIM has been a critical driver. Enterprises need more granular control over access, which has also made traditional EPMs insufficient for modern enterprise security needs. We built Cerby from the ground up to provide a more comprehensive approach to access management by extending the entire IAM lifecycle to any application. With Cerby, organizations can achieve a single control point for all their access management needs, resulting in cost savings by reducing complexity and eliminating the need for multiple solutions. This improves the organization's overall security posture and empowers employees by freeing them from managing security tasks and allowing them to focus on their core responsibilities and be more productive.
Ready to learn more about how Cerby can simplify access management and improve your bottom line? Get a free 30-day trial and say goodbye to passwords..

