Employer perceptions about applications used for work and the reality of the employees using them differ. According to our research, 92% of employees want full control over decisions about applications used for work. Because the applications employees prefer are difficult to secure and 61% of SaaS apps don’t support common identity standards, they’re often deployed without IT authorization and without regard for industry security standards putting the organization’s brands and security postures at risk.
Although the consumerization of IT is not new, recent trends around employee application choice are creating new risks–and new opportunities–for organizations and their data. Our research suggests that employers should strongly consider investigating a new approach for securing applications to accommodate this shift in employee behavior.
Implementing a new approach for securing applications can be overwhelming, so we’ve broken it down into three steps to help simplify the process.
3 steps for securing unmanageable applications
- Quantify the risk: Determine how unmanageable applications are affecting your business, and quantify it. Make it easy for stakeholders to understand the impact in financial terms. At Cerby, we often hear organizations say “we don’t have this problem,” only to realize they do after a few minutes of conversation. For example, most treasury and banking applications are single-user, and they aren’t tied to an identity provider (IdP). Identifying which applications your organization uses and whether they support industry security standards may shed new light on the state of your security posture. Leveraging existing tools such as a CASB or NGFW can help you discover just how significant the problem actually is.
- Plan: Break the problem up into smaller, more digestible chunks. Then, create a plan that leverages enrollment-based controls to manage risks. Identify a few enrollment-based solutions, and pick the best one for your business. The ideal solution should be able to help you secure unmanageable applications, bring them into compliance with corporate policies, and connect to your existing security tools and platforms.
- Scale it out: Let’s say you find out your organization is using 500 unmanageable applications, but you can’t use your existing tools to secure them because they don’t support industry and security standards. Don’t try to tackle all 500 at once! Start by identifying the top ten most used unmanageable applications. Build a plan around those ten applications, and then scale it out for the rest. Start small, track, measure, and scale.
Tip: Don’t dictate from the top down. When users start to see how enrollment-based approaches work and how beneficial they are, they’ll want to get engaged. A user-friendly, enrollment-based solution can help positively guide employees’ security behavior, no matter which applications they use.
Securing applications post-pandemic
Most organizations simply weren’t prepared for the sudden transition to remote work, and many didn’t have the technological capacity to support the change to remote users. The change impacted employers and employees alike: employees could either sit on their hands and not work or take matters into their own hands and ramp up using easily accessible cloud applications. Employers realized they needed to compromise for their employees to stay productive or risk going out of business.
A new, “make it work” mentality emerged, and with it, more freedom for employees. Quickly, responsibility for purchasing and deploying organization-wide applications went from the IT department, straight into the hands of end-users. Application developers and vendors took note of this shift in buying power, and many altered their product roadmaps in favor of prioritizing functionality over security.
Employees have been deploying applications outside the purview of IT and security departments for years–the term “shadow IT” emerged more than a decade ago to describe exactly this type of behavior. However, its definition doesn’t account for a new class of risky applications. At Cerby, we call them unmanageable applications.
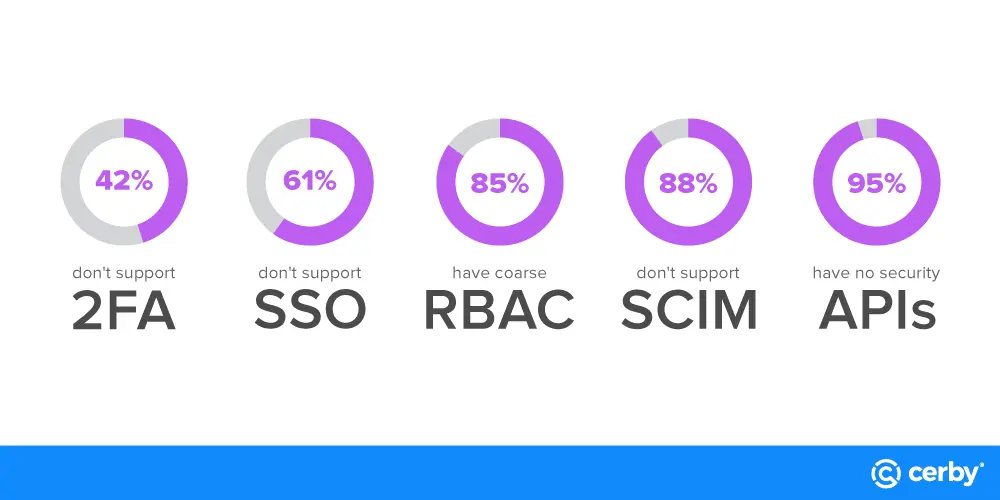
Unmanageable applications are difficult for organizations to manage because they lack security-focused Application Programming Interfaces (APIs), industry standards such as Security Assertion Markup Language (SAML) for authentication, and Systems for Cross-domain Identity Management (SCIM) for user management.
Unlike shadow IT, unmanageable applications aren’t always deployed in secret. Although they introduce risk, some organizations willingly use unmanageable applications because they also create new opportunities. For instance, according to research from Entrust, 97% of IT professionals said using their preferred technologies makes them more productive.
Governing unmanageable applications isn’t easy, but it’s becoming increasingly unavoidable for organizations. Today, our research shows that between 61-88% of applications on the market are unmanageable. As this number continues to increase, organizations are increasingly at risk of cyberattacks. Cybercriminals repeatedly go after the lowest hanging fruit, and in this case, unmanageable applications are too tempting to ignore. Over the last two years, the rise in cyberattacks targeting applications is evidence of attackers’ success, yet many organizations are still under-protected and under-prepared to recover from these types of attacks.
Real-world security risks
Here are just a few of the real-world security risks unmanageable applications introduce for organizations:
- Account takeovers: Weak passwords and disabled two-factor authentication (2FA) make it easier for attackers to guess passwords, or reuse passwords obtained from a previous data breach. Once they gain access to an enterprise account, there’s no telling what attackers might do.
- Misinformation: A successful social media attack gives attackers complete control over an organization’s social media account, where they can say whatever they want on some of the world’s largest platforms. Spreading misinformation–intentionally or otherwise–can have serious consequences for a company’s public image.
- Data breaches: Storing and processing sensitive information on unmanageable application platforms makes them more vulnerable to cyberattacks. With the average cost of a data breach in 2022 at USD $4.35 million, most organizations can’t afford the negative impacts of a successful cyberattack, including the breach of customers’ trust.
- Compliance and privacy fines: Fees for storing company data on platforms that don’t meet security standards continue to climb with the proliferation of data privacy laws. Cyber insurance premiums are also going up, and are likely to be higher for organizations using applications that cannot be centrally managed and monitored.
- Reputational damages: Most organizations have a hard time recovering their brand after a cyberattack, no matter how benign. The average consumer doesn’t know the difference between types of cyberattacks, and any kind of “attack” is seen as negative. As it turns out, the majority of consumers are willing to walk away from a brand that breaches their trust.
Existing approaches for securing unmanageable applications
Whether employees know it or not, the applications they use for work affect their employers’ security posture. To protect themselves against cyber risk, most organizations implement what’s called an “enforcement-based” approach to cybersecurity.
Often heavy-handed, enforcement-based approaches focus on preventing employees from engaging in risky behavior by establishing security policies backed by security controls. When it comes to regulating application usage, 78% of organizations have policies in place, and with the above risks in mind, it’s entirely understandable why the majority of employers take this approach.
However, policies and prohibitions may not be working as well as employers think. According to our research, although 61% of respondents at organizations with policies had applications blocked, another 51% said they would continue to use a blocked application anyway. Even with safeguards in place, employees are still using the applications they prefer.
For many organizations, this behavior creates risk around access management. Without support from employers, employees are often left to manage their own unmanageable applications and 42% of employees are responsible for managing their own passwords, even if they’re ill-equipped to do so. As a result, employees and managers are making up access management as they go, introducing risk and exposure for organizations and their data at every point of interaction.
Perhaps more surprising, we found that banning or blocking applications can have unintended consequences for employers, including negatively affecting employee job satisfaction. Most respondents view bans on their preferred applications as undermining trust, and 52% of employees want employers to “get out of the way” when it comes to choosing applications for work.
Employees are already making decisions about applications, and some employers are starting to get on board. In our research, we found that 38% of respondents at organizations with policies in place still had applications allowed. Coincidentally, organizations with this type of approach also saw positive impacts on employee engagement.
There’s a better answer for securing applications, and it involves striking a balance between two approaches on either side of the security spectrum. At Cerby, we’re calling this type of approach “enrollment-based” because it empowers employees to become more active collaborators in enterprise-wide security and compliance efforts.
When employees understand that application choice comes with responsibility, security becomes everyone’s concern. When self-enrolling and registering applications is easy, the same employees who resent policies on application choice will participate in strengthening security and ensuring compliance.