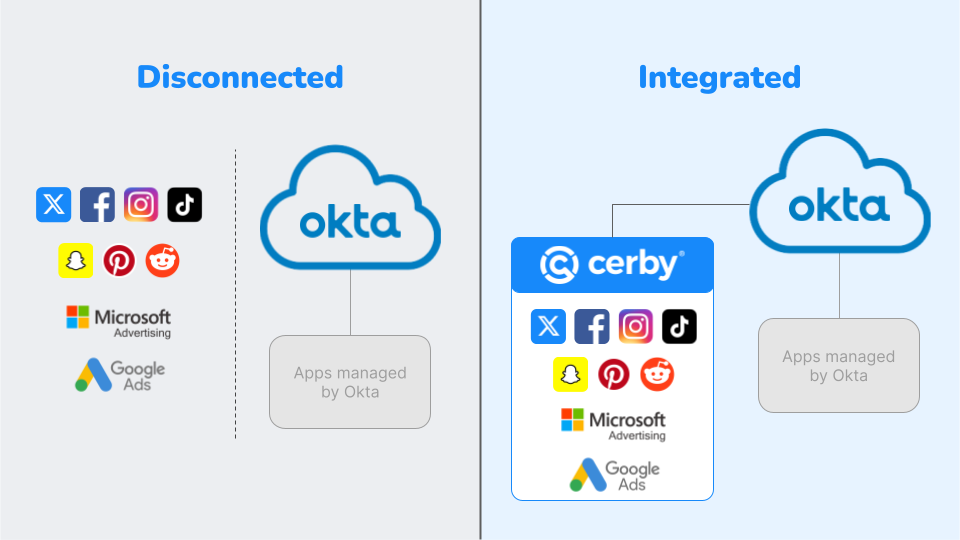
5 ways to protect ad spend
One of the biggest challenges marketers often face is protecting their ad spend across social media.
Protecting ad spend is critical for many businesses as this may be their primary marketing source, equating to hundreds of thousands or even millions of dollars per month. Given the sensitive nature and potential media exposure, if a social account is compromised, managing access to all your social media accounts is an important challenge to address.
Many companies, especially those with multiple brands, will likely have several social handles across platforms like Twitter, Facebook Business Manager, and Instagram. The risk is that teams typically manage passwords in spreadsheets, maybe even sticky notes, or in apps like Slack and Microsoft Teams. If somebody has the password and they leave your company, or maybe you're using a third-party agency… what happens when they leave? If you don't remember to change the password, they will retain access to your social media accounts.
I’ve worked with multiple customers who have had an issue where someone left the company and redirected ad spend out of their account after leaving. The company lost a lot of money because it didn’t have a good way to manage access and passwords. Not to mention a massive loss of trust with the CFO given that they did not meet key ROI metrics that quarter.
Options for protecting ad spend
When it comes to protecting your ad spend, there are a few paths that companies usually go down. Let’s go through each of them and look at the pros and cons.
- Using sticky notes
- Using Teams, Slack, or Sharepoint
- Using Google Sheets
- Using a password manager
- Using privileged identity/access management tools (PIM/PAM)
Using sticky notes
While this one might get a laugh, in a recent study, we found that 12% of employees still rely on sticky notes to manage passwords. Sticky notes (or Post-it Notes) were originally created in 1977 and have been used for all types of things. In recent years, that includes managing passwords for social media accounts.

Pros of using sticky notes
- Cheap
- Only those with physical access can see the passwords
- Can’t be breached via electronic means
Cons of using sticky notes
- Only those with physical access can see the passwords
- Does not scale well
- Will not work for agencies and third parties who need access
- Generally not considered a secure practice
Using Teams, Slack, or Sharepoint
All three of these platforms are about collaboration which could make them a good place to manage passwords. Combined, these three platforms have over 100 million users on a monthly basis. And there is a good reason: they are easy to use and typically available at companies of all sizes.
Pros of using Teams, Slack, or Sharepoint
- Easy to setup
- Low cost (most companies have one or all of these already)
- Easy to share access internally and externally
Cons of using Teams, Slack, or Sharepoint
- Anyone with access can see the passwords
- Does not enable the use of two-factor authentication
- No good way to revoke access for individuals when they leave or no longer need access
Using Google Sheets
Spreadsheets have been around for decades, but Google made sharing access to spreadsheets easy. No wonder two billion-plus people use it on monthly basis. When it comes to sharing passwords, many teams go down this route because it's easy and inexpensive. Typically an admin creates the spreadsheet, adds the accounts, and then shares it with those who need access. For many companies, this includes third-party agencies. As you can see from the spreadsheet below, this solution is easy to set up and is likely why it is one of the most popular options. But is it secure? That’s another story.
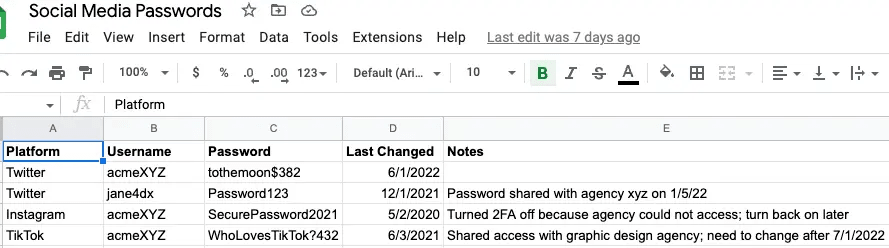
Pros of using Google Sheets
- Easy to set up
- Low cost
- Easy to share access
- Access to the spreadsheet can be secured with two-factor authentication
Cons of using Google Sheets
- Anyone with access to the spreadsheet can see all the passwords
- Employees or third parties (agencies or contractors) have the password even after they leave
- Typically means disabling two-factor authentication to the individual applications
Using a password manager
Using a password manager is typically considered the most secure of the options above. There are many good ones out there like 1Password, Dashlane, LastPass, etc. Password managers are able to securely store all your passwords in a vault, typically on your local computer or in the cloud (or both!). Instead of having to remember dozens or hundreds of passwords, you only need to remember one. The master password. While all this sounds great, is it a good solution to manage access to your social media accounts?
Pros of using a password manager
- Cost-effective
- Enterprise options available
- Secure
Cons of using a password manager
- Does not address shared two-factor authentication
- Difficult to scale beyond a single person
- Does not help third parties who need access
- Not easily tied in with corporate identity providers like Okta and Azure Active Directory for provisioning and deprovisioning of shared accounts
Using privileged identity/access management tools (PIM/PAM)
Accounts with powerful access, like social media and admin accounts, are often the target of attackers. Verizon’s Data Breach Investigations report found that over 80% of breaches involved brute force (trying many different passwords to unlock an account) using lost or stolen credentials. If one of these credentials is from an account that has full access to your social media presence (or your encryption keys, etc.), then the impact could be devastating. A common way to manage access to these types of sensitive accounts is through PIM/PAM tools. Leading vendors include JumpCloud, CyberArk, and BeyondTrust.
Pros of using PIM/PAM
-
Strong access controls
-
Mature technology
-
Widespread integrations with existing security tools
Cons of using PIM/PAM
- Requires end-users to learn a new tool that may not be user-friendly
- Weak to no out-of-the-box integrations with many social platforms
- No automated remediation of common social media security hygiene tasks, e.g., enabling 2FA, strong passwords, etc.
Protecting ad spend is an ever-evolving landscape
Social media advertising is the second biggest market in digital ads worldwide, with revenues of $153 billion in 2021 and is expected to grow to over $252 billion in 2026, according to Hootsuite. With this much money on the line, companies need a secure approach to managing access to social media. As you learned above, there are many options for securing your ad spend, but none of them are without their drawbacks. Businesses will need to weigh the pros and cons of each option and then make an informed decision.